Zero Networks Launches a New Free Tool to Help Companies Assess Their Exposure to Risks Due to Excessive Network Access
We are excited to introduce a new free tool, the Zero Networks TrustMeter, that shows you just how much an attacker will be able to access if they get into your network. This gives you much needed visibility into your network’s security stance, so you can take steps to mitigate your exposure to unnecessary risk.
As organizations around the globe rush to enable remote work for their employees, cybercriminals are taking advantage of the expanded attack surface to get into your network. The World Health Organization reported they have seen a fivefold increase in cyberattacks over the past months, which is indicative of the increased attack activity that organizations everywhere are seeing.
How exposed is your network? How do you even know?
Those are questions almost every organization is wrestling with. Unfortunately, the answers are never straightforward. Given the complexity and dynamic nature of today’s networks, it can be extremely difficult to gauge what an attacker will be able to do when they get into your network. Until now.
The Dangers of Excessive Trust
TrustMeter Use Cases
How TrustMeter Works
How to Use TrustMeter
How to Read a TrustMeter Report
Looking Forward
It is important to note that all data collected during TrustMeter’s scan remains local on the machine from which it run, it is not uploaded anywhere.
The Dangers of Excessive Trust
Most organizations concede their network is too open, allowing users inside to access way more than they will ever need or ever should be able to access. Our CEO, Benny Lakunishok, explains, “This excessive trust means that once an attacker compromises one machine inside the network, it’s easy for them to go anywhere and do whatever they want in the network. As a result, IT and security teams end up not being able to trust their own networks.”
If not addressed, excessive network access enables VPN infiltration, lateral movement, zero day exploits, and ultimately data exfiltration, as well as the spread of commodity malware and ransomware. With so much at stake, what can you do to start to tackle the problem?
You can begin by getting a clear view of how much your network is open from the inside, so you understand how exposed you may be. To help you do this, we are excited to announce TrustMeter, a free network segmentation tool you can use to quickly and easily map excessive trust within your network. In just a couple clicks, TrustMeter gives you insights into just how much an attacker could access in your network, with data you can use to take proactive action to limit infiltration damage.
TrustMeter Use Cases
Running TrustMeter from different locations inside the network will yield different results because network access can change based on where you are in the network. Therefore, we recommend running TrustMeter in a number of different locations to uncover the biggest “soft spots” of your network. For example, you will probably want to see where an attacker could spread to from these spots in your network:
- Remote workers (including VPN access) - the recent shift to a more mobile workforce and the rise of VPN use has made networks more vulnerable than ever. The increased home workforce has created a much larger attack surface for an attacker to exploit to get into the network or spread malware. TrustMeter can scan the network from a VPN client’s machine to reveal how much is vulnerable to an attacker that is entering the network from that VPN.
- Client networks - a single compromised client machine can easily spread malware throughout a network. TrustMeter can scan the network from an internal host to give you complete visibility into which assets are accessible from a single machine inside the network.
- Machines inside the Data Center - it’s well known that public facing resources can be compromised and used as a stepping-stone for the entire network. TrustMeter can scan the network from the data center, giving you “inside-out” visibility into problematic network paths. Warning - the results tend to be surprising.
How TrustMeter Works
TrustMeter extracts assets and identity information and actively scans all assets to provide you detailed information on what is open and vulnerable to exploitation. Scans can be run from any machine in the network. TrustMeter will then generate a report which will provide clear visibility into the entire network from that vantage point.
The information is collected and processed to show you:
- Which assets are accessible to an attacker and which are not from the executing machine
- What are the most commonly accessible services across the network
- Which assets are clients and which are servers
- Which IP ranges are homogenous, which means they are made up of only clients or servers, and which are “mixed”, which means they are made up of both clients and servers
Finally, three files are outputted by TrustMeter:
- Report.html - provides an easy to understand visualization of the analysis based on the data collected. This is the main output, so it is designed to be simple to consume and share.
- Networks.xlsx - delivers granular statistics on the composition of the different IP ranges examined
- Assets.xlsx - presents the detailed data gathered on all of the assets found in the network, including their categorization of clients or servers.
How to Use TrustMeter
Quick Start
TrustMeter is designed to be simple to use. The default configuration works out of the box for most use cases. To get started, you should:
- Download the tool.
- Copy the TrustMeter tool onto the machine, according to your use case (VPN, data center, etc.)
- Run the tool and let the entire scanning process complete.
- Upon completion, TrustMeter will automatically generate and open the html report.
- In this first version, TrustMeter can be executed from Windows 7 operating system or higher, and from Windows Server 2008 or higher.
- The TrustMeter report can be viewed in Chrome, Firefox or Edge. Depending on your organization‘s size, the tool may need several seconds to several hours to complete the mapping process. There are processing bars that will keep you apprised of its progress to make the waiting time more predictable (and enjoyable!).
Advanced Settings
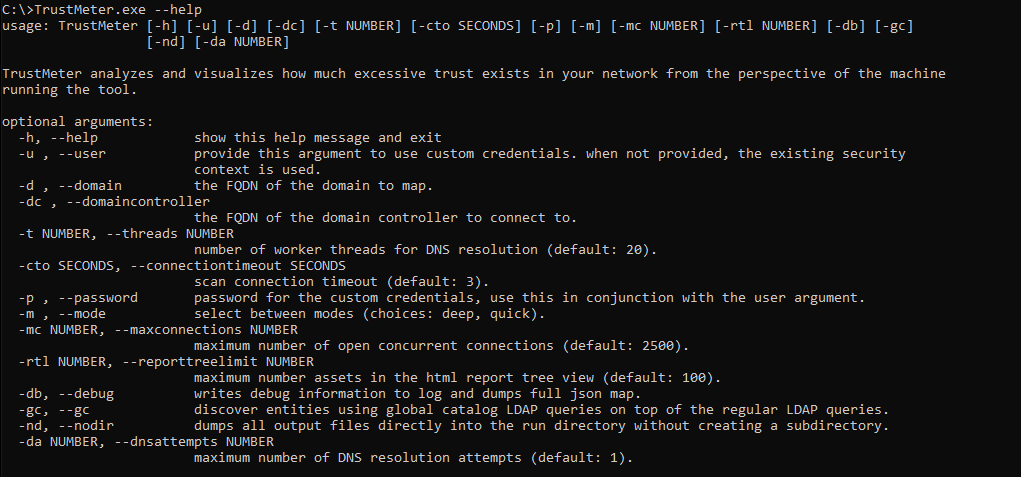
While the tool should run out of the box, there are advanced configuration parameters you can use to fine-tune the tool based on your individual environment. While there are numerous parameters that can be configured, the two most critical for the quality of the results are maxconnections and mode:
- Maxconnections controls the maximum number of network connections that can be open simultaneously during the scan. More open connections equates to a faster scan, but it can also affect accuracy for those networks that have a lot of unpredictability. For those networks, we recommend lowering the default setting of 2,500 to ~500 connections. On the flip side, for those networks with fast and reliable connections, we recommend increasing the number up to 7,500 connections.
- Mode controls the amount of ports scanned. The default configuration is set to “quick,” which delivers an efficient mix of fast execution time and clear visibility into all assets. For more details on excess network access and services, you can adjust the setting to “deep” mode. This mode will take longer, but will provide additional details; it is recommended for smaller environments or extremely fast and reliable networks.
Additional parameters are available and detailed in the help menu.
How to Read a TrustMeter Report
TrustMeter reports are divided into three sections, which will provide you differing levels of detail and insights.
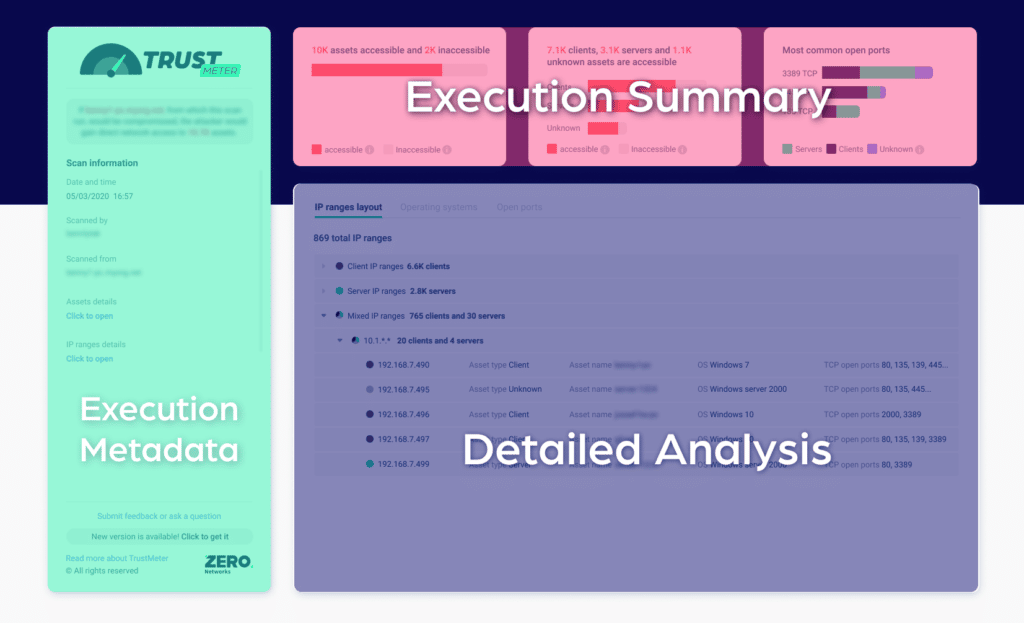
- The Execution Metadata appears in a rectangular box down the left side of the first page. This section contains basic information about:
- The executing user
- The machine that ran the scan
- The scan mode
- Any other relevant parameters of the scan
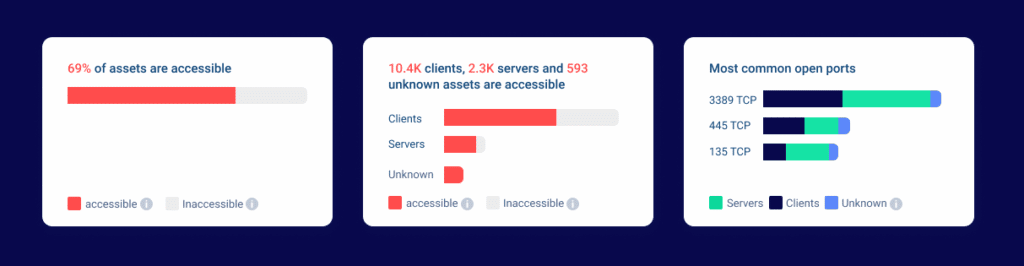
- The Execution Summary is contained in the smaller rectangular boxes across the top of the first page. This section presents the network accessibility data in an easily digestible, concise summary of collected results. Things of note include:
- The percentage of assets that are accessible - The first rectangular box displays probably the most critical finding, namely the percentage of assets that an attacker could access if they are in your network. This number is derived from the percentage of assets that we could resolve in the environment and that can be accessed over the network.
- Asset breakdown - The second box breaks down the accessible assets by operating system type, so you know whether they are clients, servers, or unknown.
- Ports - The last box delivers analysis of the most common accessible ports by either clients, servers, or unknown devices in the network.
- The Detailed Analysis is located in the long rectangular box across the bottom of the first page. It breaks down the mapped data from three different perspectives:
- IP Ranges - environments have specific subnets for clients, servers, and different sites. These configurations tend to change over time, so this view helps you identify subnets that shouldn’t be accessible due to IP range or asset makeup.
- Operating Systems - This view groups all assets based on their operating system (OS) prevalence, which can be helpful when identifying a misplaced OS that should not be accessible from your scanning host or when trying to find old OS that shouldn’t be present in your network.
- Opened Ports - This view groups accessible ports by their prevalence, which can be helpful when identifying services that shouldn’t be exposed.
Looking Forward
Knowing what you’ve got is just the first step when trying to figure out how to successfully manage network access. TrustMeter’s holistic report provides vital insights into how much excessive access exists inside your network and which assets could be compromised in an event of a cyberattack, so you can take steps to mitigate your risks and shut down these internal attack vectors.
If you would like to solve the problem of excessive trust that TrustMeter revealed, we are happy to help. It probably warrants another conversation and definitely another blog - so please reach out.



