TL;DR
Network segmentation divides a network into smaller subnetworks to enhance security, control access, improve performance, simplify management, and aid regulatory compliance by isolating critical systems and data flows. Key methods for achieving network segmentation include VLANs, subnets, access control lists, internal firewalls, and physical separation of network infrastructure.
What is Network Segmentation?
Network segmentation is a fundamental strategy in network security that involves dividing a larger network into smaller subnetworks, or segments. Each segment functions as an isolated entity, with its own set of security controls and policies, creating boundaries that limit the ability of threats to move laterally within the network. This can be accomplished through both physical segmentation, where separate network devices and hardware are used, and virtual segmentation, which utilizes network virtualization to achieve the same effect.
By segmenting the network, administrators can improve network performance, control access to sensitive resources, reduce the attack surface, and better protect against potential threats. Additionally, network segmentation plays a crucial role in regulatory compliance, as it allows for granular control over user access and ensures the security and integrity of critical data and intellectual property. Overall, network segmentation is an essential practice that enhances both the security and efficiency of network infrastructure.
Network Segmentation Benefits
Network segmentation offers several key benefits to organizations in terms of security, regulatory compliance, performance optimization, and simplified maintenance.
By dividing a network into smaller segments, the scope of unauthorized access is limited, reducing the likelihood of lateral movement by attackers. This increases the overall security posture of the organization, ensuring that potential threats are contained within specific segments and minimizing potential damage.
Furthermore, network segmentation aids in maintaining regulatory compliance by creating boundaries for sensitive data and implementing necessary security measures for each segment. This helps organizations meet industry regulations and protect intellectual property.
Additionally, network segmentation improves network performance by reducing congestion and optimizing traffic flows, thus enhancing the overall user experience.
Finally, it simplifies troubleshooting and maintenance activities by allowing network administrators to isolate and address issues within specific segments without impacting the entire network.
Although network segmentation offers "better security" by limiting unauthorized traffic and lateral movement, it is only a starting point. While it surpasses having no segmentation at all, it doesn't match the effectiveness of microsegmentation in safeguarding organizations from severe cyber threats like ransomware.
Reduced Attack Surface. Network segmentation plays a pivotal role in minimizing the scope of a cyberattack by reducing the attack surface. By dividing a network into smaller segments, each with its own dedicated resources and security controls, the potential impact and extent of a cyberattack are significantly reduced.
When an attacker gains unauthorized access to a segment, network segmentation ensures that their activities remain isolated within that specific segment. This isolation prevents the attack from spreading to other segments or critical systems within the network. As a result, the attacker's ability to move laterally across the network is impeded, minimizing the overall damage they can cause.
By isolating the attack within a single segment, network segmentation effectively reduces the attack surface. Rather than having an entire network exposed to a cyberattack, only a specific segment is compromised. This significantly narrows the scope of the attack, making it easier for network administrators to contain, investigate, and mitigate the impact of the incident.
In addition to isolating attacks, network segmentation also allows for tailored security measures and access control policies within each segment. This ensures that even if one segment is compromised, the security measures in place within other segments remain intact, preventing unauthorized access to critical resources.
Protect Critical Assets and Devices and Enable Easier Maintenance. Network segmentation stops attackers from reaching parts of the network that are mission-critical for your organization but may not have advanced security measures of their own. For example, a hospital may deploy network segmentation to protect lifesaving medical devices from attacks.
Furthermore, network segmentation significantly contributes to easier troubleshooting and maintenance of a network. By dividing a network into smaller segments, network administrators can isolate specific areas and easily identify and address issues that may arise. When a network issue occurs, it can be localized to the specific segment where the problem is originating, reducing the scope of troubleshooting efforts. This targeted approach saves time and resources, allowing for quicker resolution of network issues.
Automating network segmentation further enhances troubleshooting and maintenance processes. By implementing tools that can automatically identify and classify new assets and data, network administrators can quickly adapt to changes within the network. This automation streamlines the process of segmenting the network, eliminating manual effort and reducing the chances of human error.
Improved Network Performance. Network segmentation is a crucial strategy for enhancing overall network performance. By dividing a larger network into subnetworks or segments, organizations can effectively reduce network congestion and control the flow of traffic. This segmentation policy helps ensure that each segment is responsible for a specific set of tasks, preventing overcrowding and enabling smoother data transmission.
By limiting the number of connected devices within each subnet, network administrators can significantly improve network performance. When there are fewer devices competing for network resources, the overall speed and efficiency of the network increases. With reduced network congestion, data packets can travel more quickly, leading to faster response times and improved user experience.
Additionally, network segmentation allows for better traffic control. By separating different types of traffic, such as internal and external, organizations can prioritize critical data flows and allocate resources accordingly. This level of control enables seamless communication and minimizes the risk of bottlenecks or slowdowns.
Simplified Regulatory Compliance. Regulatory compliance is of utmost importance in the context of network segmentation. It refers to the adherence of an organization's network and security practices to industry-specific regulations and standards. Implementing network segmentation helps organizations achieve and maintain regulatory compliance by ensuring proper management of vulnerabilities, permissions, and updates.
Segmentation plays a crucial role in compliance as it allows organizations to segregate sensitive data and resources into distinct segments, each with its own set of security controls and access policies. By separating and isolating data based on regulatory requirements, organizations can easily identify and manage the systems that fall within the scope of compliance initiatives. This reduces the complexity of compliance efforts and enables efficient monitoring and auditing procedures.
Moreover, network segmentation ensures that only necessary components are subject to compliance requirements, reducing the costs associated with implementing and maintaining compliance measures. Instead of applying costly and time-consuming controls to the entire network, organizations can focus their resources on securing and monitoring only the segments that handle regulated data or perform critical functions.
Regular audits are essential in maintaining regulatory compliance within segmented networks. These audits help identify vulnerabilities, ensure that proper permissions and access controls are in place, and verify that software and firmware updates are promptly applied across all segments. By regularly auditing segmented networks, organizations can proactively address any compliance gaps or weaknesses and ensure ongoing adherence to regulatory requirements.
Increased Security. Increased security is one of the primary reasons why network segmentation is essential for organizations. By dividing a larger network into smaller segments, network administrators can effectively limit the scope of potential threats and prevent attacks from spreading throughout the entire network.
Network segmentation acts as a critical barrier to block the lateral movement of malicious actors within the network. By isolating different segments, even if one segment becomes compromised, the rest of the network remains protected.
This prevents the infiltration of malware, ensuring that it cannot spread to critical systems and compromise sensitive data or intellectual property.
Physical Separation of Users and Services. Physical separation is a crucial aspect of network segmentation as it plays a significant role in creating an isolated island within a larger network. By physically separating users and services into distinct segments, the risk area for attackers is minimized, effectively reducing the potential damage they can cause.
A physically separated network creates a barrier that limits lateral movement and prevents unauthorized users from accessing critical resources. It creates an environment where each segment operates independently, with its own access control lists and security policies. This isolation effectively contains any potential threats, limiting their impact to only the segment they have breached.
The benefits of physical separation extend to both functionality and security. From a functionality perspective, it allows for optimal resource allocation and performance. Each segment can be tailored to meet the specific demands of its devices and services, ensuring efficient usage of network resources and preventing network congestion.
In terms of security, physical separation enhances access control and reduces the attack surface. It limits the scope of compliance and regulatory requirements to a specific segment, making it easier to implement and maintain security measures. Additionally, physical separation allows for the implementation of dedicated hardware and secure communication channels, further bolstering the network's security.
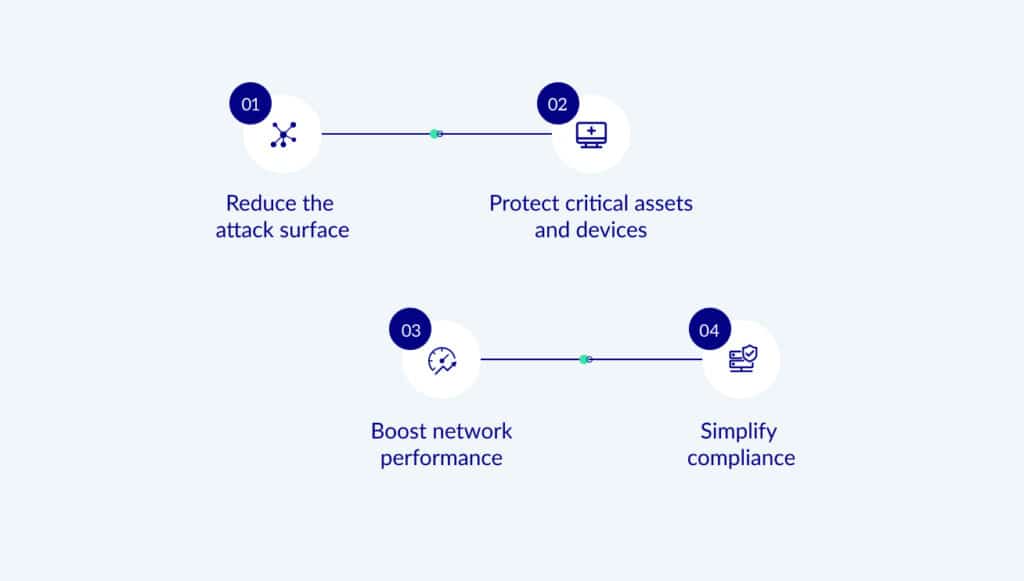
The Key Benefits of Network Segmentation
Types of Network Segmentation
There are different types of network segmentation that can be implemented depending on the specific needs and requirements of an organization.
One common type of network segmentation is logical segmentation, where virtual networks are created within a larger network. This allows for different departments or user groups to have their own virtual network, with separate security policies and access controls. Logical segmentation is particularly useful in multi-cloud environments, where different cloud providers can be assigned their own virtual segment.
Another type of network segmentation is physical segmentation, where the network is physically separated into independent segments using dedicated hardware and physical infrastructure. This provides a higher level of security as it creates a physical barrier between segments, preventing unauthorized access and limiting the spread of any potential threats. Physical segmentation is often used in larger networks with strict security requirements, such as those handling sensitive data or intellectual property.
Perimeter-based segmentation is another approach to network segmentation, whereby the network is divided into different segments based on the network perimeter. This allows for different levels of access control and security measures to be implemented based on the level of trust associated with each segment. For example, segments with external facing resources may have stricter security measures compared to internal segments.
Crucial Aspects of Network Security and Segmentation
Lateral Movement Prevention. Lateral movement prevention is a crucial aspect of network security, and network segmentation plays a significant role in achieving this goal. By dividing a network into subnetworks or segments, network administrators can isolate different areas, making it more challenging for attackers to move laterally from one segment to another.
Network segmentation limits the potential spread of attacks by creating barriers between segments. If an attacker gains unauthorized access to one segment, they will be contained within that segment and unable to freely move throughout the entire network. This reduces the attack surface and minimizes the potential impact of a security breach.
To enforce this isolation, internal firewalls and access control lists (ACLs) are often implemented within the segmented network. Internal firewalls act as additional security measures, preventing unauthorized lateral movement between segments. ACLs work alongside internal firewalls by defining the traffic flows allowed between segments, tightly controlling the communication between them.
By incorporating network segmentation with internal firewalls and ACLs, organizations can strengthen their security posture and significantly reduce the risk of lateral movement. This approach compartmentalizes the network, making it more challenging for attackers to navigate and escalating the difficulty of their malicious activities.
Access Control Lists (ACLs). Access Control Lists (ACLs) play a crucial role in network segmentation by controlling and filtering network traffic based on predetermined rules. In the context of network security, ACLs are used to manage user permissions and restrict access to sensitive data.
ACLs work by defining rules that determine which traffic is allowed or denied between segments. These rules can be based on various criteria such as source and destination IP addresses, port numbers, protocols, or specific user identities. By enforcing these rules, ACLs ensure that only authorized traffic is allowed to pass between segments, while malicious or unauthorized traffic is blocked.
In terms of managing user permissions, ACLs allow network administrators to grant or restrict access to specific resources or services within a segmented network. By setting up ACLs, administrators can define who can access certain network resources and what actions they are allowed to perform. This fine-grained control helps to prevent unauthorized access and limit the potential damage that can be caused by malicious actors.
Network Perimeter Defense. Network perimeter defense is a critical aspect of network segmentation that helps protect an organization's network from external threats. It involves establishing a secure boundary around the network to prevent unauthorized access and potential breaches.
Firewalls and access control lists (ACLs) play a vital role in establishing a secure network perimeter. Firewalls are security devices that monitor and control incoming and outgoing network traffic. They examine the traffic based on predefined rules, thereby allowing or blocking certain connections. ACLs, on the other hand, work within the segmented network to control traffic flow between the different segments. By defining and enforcing rules, ACLs ensure that only authorized traffic is allowed to pass, thereby reducing the attack surface.
Traffic Flow Isolation. Traffic flow isolation is a key concept in network segmentation that focuses on separating different types of traffic within a network. By categorizing and isolating traffic flows, organizations can enhance both network performance and security.
When implementing traffic flow isolation, network administrators assign specific segments or subnetworks to different types of traffic, such as user, management, or data traffic. This segregation prevents potential threats from spreading across the network. For example, if a user device is compromised and becomes a source of malicious traffic, traffic flow isolation ensures that this traffic is contained within its designated segment and does not impact other parts of the network.
One of the main benefits of traffic flow isolation is improved network performance. By separating traffic types, organizations can allocate resources more efficiently and prioritize critical traffic. This helps prevent network congestion and ensures that essential applications and services operate at optimal levels.
Traffic flow isolation also strengthens network security. By containing and isolating different traffic flows, the impact of any security incidents or breaches is limited. In the event of unauthorized access or suspicious behavior, the segmented nature of the network prevents lateral movement, making it more challenging for attackers to navigate and exploit the system.
Logical Topology Changes. Logical topology changes in network segmentation enable organizations to reconfigure their network structure without the need for the physical movement of components. This approach allows for increased flexibility and scalability in managing network resources.
One way to achieve logical segmentation is through the use of Virtual Local Area Networks (VLANs). VLANs allow the creation of multiple virtual networks within a single physical network infrastructure. By assigning specific ports, switches, or users to different VLANs, organizations can effectively isolate traffic and control access to network resources. This simplifies network management and ensures that devices within the same VLAN can communicate with each other while remaining isolated from devices in other VLANs.
Another approach to logical segmentation is through network addressing schemes. By dividing a larger network into subnets, organizations can create distinct segments with their own subnet address ranges. This allows for efficient management of IP addresses, as well as the ability to enforce access control and security policies at the subnet level. The provisioning and configuration process can also be automated through the use of network addressing schemes, reducing human error and streamlining network operations.
Overall, logical topology changes in network segmentation provide organizations with the flexibility to adapt their network structure to changing needs without the limitations of physical hardware movement. VLANs and network addressing schemes offer effective methods for creating subnets and automating provisioning and configuration processes, enhancing network management and security.
Network Segmentation Challenges
Historically, implementing network segmentation tools has been costly and difficult. Some of the older approaches include internal firewalls, Access Control Lists (ACL), and Virtual Local Area Networks (or VLANS). These approaches are outdated and cumbersome. Besides the large expense of buying special hardware and maintaining it, today’s network is more dispersed (both on-prem and in the cloud), making these traditional approaches largely ineffective anyway.
With this hybrid network, the perimeter is blurry and therefore impossible to effectively secure with a traditional hardware perimeter-based approach. And, since these old-school segmentation methods are typically based on trust (meaning whatever is inside the network or network region is trusted and everything outside is not), it means there is little to stop an attacker if they are able to breach the perimeter.
Network Segmentation vs. Microsegmentation
To reiterate our point from earlier, network segmentation is better than no segmentation, but it is far from good enough when it comes to protecting an organization's network from attacks and lateral movement. While it can help organizations shrink their attack surface, protect their critical data, and improve their network’s performance, the old hardware-based perimeter model of network segmentation has many flaws. This is because even within segmented networks there are many opportunities for attackers to do damage (and eventually reach everything in the network).
For example, if an organization segmented its network by functional department, and an attacker managed to breach their finance department, that attack would still be catastrophic to the organization. The attack would also likely reach at least one machine it could use to traverse to other network regions, and then repeat the process to reach most –if not all – the network eventually. This is because network segmentation, while a great direction for organizations to go, doesn’t go far enough to really stop attackers.
So, what do organizations need to do to stop these attacks? The answer is microsegmentation.
Microsegmentation—the process of isolating all clients, workloads, applications, virtual machines, and operating systems into individual protective barriers that cannot be penetrated by attackers—is a much more granular and robust way to protect an organization. And it actually works when it comes to stopping attacks. Microsegmenting a network makes it virtually impossible for attackers to move laterally within the network and cause damage. The attack surface is reduced to virtually nothing.
The Zero Networks Solution
Zero Networks provides an automated microsegmentation solution that adapts to your environment, keeping only the necessary connections between machines open. By leveraging adaptive MFA (Multi Factor Authentication), normal usage for non-admin users is uninterrupted (attackers do not use that to spread), while the rest (admin users) require MFA for temporary access.
Zero Networks virtually eliminates your network’s attack surface with no manual segmentation or rule manipulation, and no agents.
The benefits of automated microsegmentation:
- Isolate everything (down to the individual machine) with a single click and no friction
- Prevent 99.9% of attacks. Stop lateral movement without interrupting normal network traffic
- Scalable for any size organization, without the need for agents or manual operation
- Streamline security operations; reduce the cost of NACs, internal firewalls, IPS and manual ACL-based microsegmentation
- Stay compliant with cyber insurance policies
Microsegmentation means that every module in the environment should only be able to access the information and resources necessary for legitimate purposes. Great idea – in theory – that few organizations practice. Sadly, past efforts at microsegmentation required cumbersome agents, hair pinning, or expensive professional services.
Zero Networks, instead, found a new paradigm that proves that microsegmentation can be fast, easy, effective, and deployable by anyone to get military grade security. Reduce the risk of breaches to almost zero with Zero Networks’ MFA-based microsegmentation solution. Request a demo today.



