TL;DR -
Zero Trust Network Access (ZTNA) provides secure remote access without opening any ports to the internet. It enforces granular access policies based on user identity, device health, and context to prevent unauthorized access and reduce the attack surface. ZTNA is an evolution of VPN providing enhanced security for modern distributed workforces.
What is Zero Trust Network Access (ZTNA)?
ZTNA is an evolution of the Virtual Private Network (VPN) to allow for remote access in a more secure way without having to open any port of the remote access server to the outside world, which is usually used by hackers to get in using vulnerabilities.
Why is Zero Trust Network Access important?
In today's cyber threat landscape, attacks continue to be on the rise against organizations large and small. Cybersecurity & Infrastructure Security Agency (CISA) stated “Ransomware tactics and techniques continued to evolve in 2021, which demonstrates ransomware threat actors' growing technological sophistication and an increased ransomware threat to organizations globally.” Attackers continue to gain access through phishing, vulnerabilities, brute force attacks, and stolen credentials.
In order to increase resiliency and reduce risk from compromise, the adoption of a Zero Trust approach, which means no ports should be open before verification of the identity needs to be achieved from both inside and outside, and the ZTNA helps to achieve that from the outside by having a secure remote access solution that doesn't need any open port on the internet to allow for users to remotely connect to the organization and get access to internal applications and services.
Zero Trust Network Access vs VPN
Virtual Private Network (VPN) is a technology that was created to allow remote workers access to internal networks. Typically, the VPN client establishes a connection that is authenticated creating a tunnel for traffic to flow over. This tunnel allows the endpoint to access resources as if it were connected to the organization's network. The following diagram depicts a typical VPN architecture.
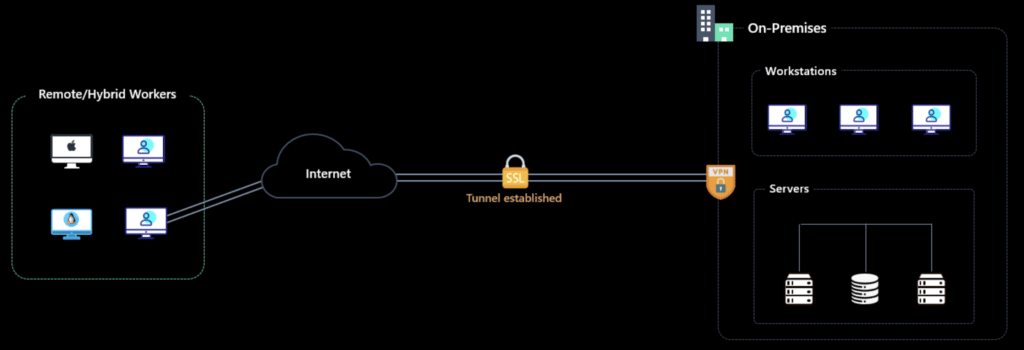
The problem with this architecture is mainly that VPN port must be open to the internet, and everyone can try to hack it with known vulnerabilities that weren’t patched yet or unknown vulnerabilities that can’t even be patched also as traditional VPNs were implemented there is no device and user awareness and the access that is granted is absolute to the entire network.
“ZTNA, on the other hand, integrates device compliance and health into access policies, giving organizations the option to exclude non-compliant, infected, or compromised systems from accessing corporate applications and data” according to SC Magazine. ZTNA policies can consider various contexts like device state, identity state, location, application used, etc. allowing for complex decisions on whether to allow certain access or not. The following depicts a typical ZTNA architecture.
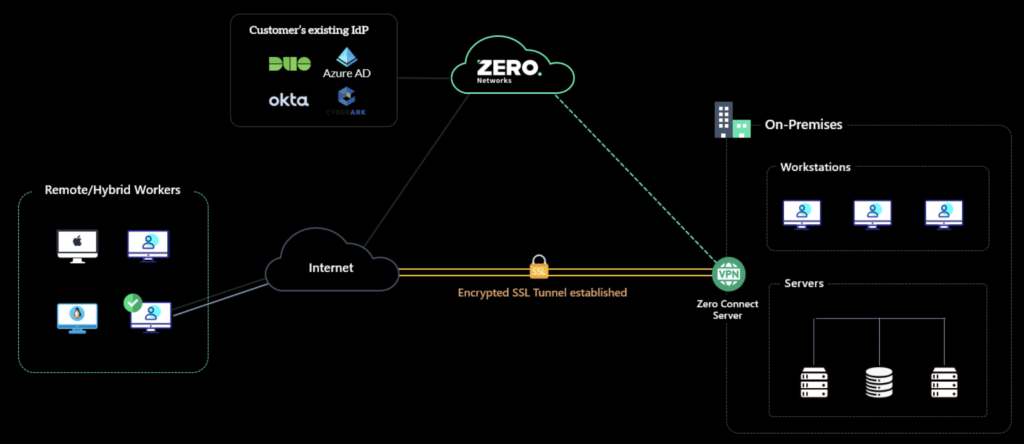
Here the ZTNA provider can leverage an existing Identity Provider (IdP) as a policy decision point and the ZTNA server acts as the policy enforcement point. Meaning based on the information provided from the IdP like device health the ZTNA provider might allow or deny the connection to resources.
Benefits of ZTNA
The benefits of ZTNA are a must for the enterprise and include the following:
- Reduce attack surface as ZTNA doesn’t need to be exposed to the internet like traditional VPN
- Centralized policy control for resource access
- Granular access control with context awareness
There are some challenges that come with ZTNA to allow these benefits. It is important to create the right policies mapping who needs what access to which resources. It could be easy for an organization to oversimplify and grant too much access when it's not needed. Ideally, the ZTNA provider could leverage some type of learning engine to map this for the organization. End user friction could also create pushback on the change to use ZTNA. If policies are not configured correctly the user may lose access to something that is needed or required to do their job.
ZTNA Use Cases
Organizations may have one or more of the following use cases for ZTNA:
- VPN Replacement: Controlled remote access to provide zero trust access to organization resources when working remotely.
- Vendor secure remote access: Controlled remote access to provide zero trust access to organization resources for vendors and third-party users.
- Application Access: Control access to applications that are hosted on-prem or cloud. This could include SaaS, IaaS, PaaS, or any custom application.
- Micro-segmentation: Securely segment resources and grant access based on user/device context.
- Data Protection and Privacy The shift to ZTNA has many implications when it comes to data protection and privacy. It is now possible to create policies that are based on identity information including the context in which the user is accessing resources. This allows organizations to control who can access what, where, and when. For example, a policy could be created to ensure only specific users can access data in a specific location or using a certain device type. This granular control can greatly reduce the risk of data leakage and ensure that only authorized individuals are allowed access to sensitive data. Additionally, other controls such as time-based access restrictions can be implemented to further protect data from unauthorized access.
Zero Trust Network Access (ZTNA) is becoming increasingly popular for organizations wanting to secure their networks and data. It provides a range of benefits, such as reducing attack surfaces, providing centralized policy control, and granting granular access with context awareness. In order to make the most out of ZTNA, organizations must review their current technologies and solutions in place to determine where they can replace them with a zero-trust approach. ZTNA can also help organizations comply with data privacy regulations such as GDPR and CCPA.
A successful Zero Trust Network Access (ZTNA) deployment requires a robust security strategy and implementation of the right technologies. Organizations must first assess their security posture and identify areas of risk that can be addressed with ZTNA. This requires an understanding of the network architecture, user access requirements, and the data being accessed. Once these items are identified, it is essential to ensure the appropriate authentication methods, encryption technologies, and monitoring tools are in place to ensure secure access. Additionally, organizations should ensure they have the right policies and procedures in place to protect data from unauthorized access. Organizations that implement ZTNA can gain enhanced security for their networks while also providing a better user experience through more granular access control.
Each organization will need to consider current technologies or solutions in place vs requirements of policies and controls to determine where ZTNA could replace existing costs and create a better security posture. At some point, it will be required to move to a ZTNA technology as part of a larger Zero Trust strategy and the need to reduce the risk of compromise to an organization.
We heard this firsthand from John Shaffer the CIO of Greenhill, “Related to the trends that I mentioned earlier (loss of privacy, the rise of the fully digital/remote workplace), the attack surface for the enterprise is greater than it has ever been.” No matter which use case is being evaluated, the trusted network model is too much attack surface the attacker could leverage to spread in an organizational network. ZTNA is the solution to reduce that attack surface.
More FAQs about ZTNA
What is a Zero Trust Architecture
Zero trust architecture (ZTA) is an approach to cybersecurity that assumes that all internal and external actors are untrustworthy and no network or system is safe from attack. It was developed as a response to the traditional "castle and moat" security strategy, which is based on the assumption that the perimeter of an organization should be secured in order to keep out malicious actors. The goal of ZTA is to protect an organization’s data and systems from unauthorized access or modification, no matter where the user is located.
What Is Zero Trust Network Access?
Zero Trust Network Access (ZTNA) is an approach to cybersecurity that implements advanced access control policies across all networks, users, and systems. It requires all users attempting to access corporate resources to authenticate their identity and verify the device they are using before granting them access. This ensures that only authorized users can gain access to sensitive data and systems. The ZTNA approach also enables organizations to set granular access policies that restrict user access to specific resources and locations.
Can ZTNA be used in the Cloud?
Yes, ZTNA can be used in the cloud. In fact, many organizations are leveraging it for their cloud deployments. By using ZTNA, organizations will be able to set granular access policies that are tailored to the individual user or device. This allows them to control who has access to which resources in the cloud and prevent unauthorized users from gaining access. Additionally, ZTNA can provide additional security measures such as user authentication and device health checks, which can help to further reduce the risk of a breach.
Can ZTNA help control access to applications?
Yes, ZTNA can help control access to applications. By leveraging the various contexts that can be taken into consideration with ZTNA policies such as device state, identity state, location, application used etc., organizations are able to have granular control over who is accessing which applications. This enables organizations to remove access rights for users who are not fully compliant or whose device is compromised and vulnerable.
What is lateral movement related to ZTNA?
Lateral movement is a critical concern related to Zero Trust Network Access (ZTNA). It occurs when an attacker is able to move from one system or device to another within a network without being detected. This allows the attacker to gain access to valuable data, networks and systems. ZTNA can help prevent lateral movement by controlling access privileges based on user identity, device health checks and other contextual information. This helps mitigate the risk of an attacker being able to move freely within a network.
Does Zero Trust Network Access (ZTNA) Help Protect Remote Users?
Zero Trust Network Access (ZTNA) helps protect remote users by providing granular access controls that are tailored to the individual user or device. This allows organizations to limit access to certain resources based on user identity, device health checks, and other contextual information. This prevents unauthorized users from gaining access and reduces the attack surface that attackers can leverage. Additionally, ZTNA can provide additional security measures such as user authentication and device health checks, which can help to further reduce the risk of a breach.
Can ZTNA help control the visibility of an asset?
Yes, ZTNA can help control the visibility of an asset. By leveraging granular access policies, organizations are able to limit user access to certain resources based on identity, device health checks, and other contextual information. This allows organizations to control who is able to view or access a specific asset as well as who has the ability to modify or delete it. This helps reduce the risk of data leakage and unauthorized access.
What is the best use of VPN vs ZTNA in a Corporate Network?
The best use of VPN vs ZTNA in a corporate network depends on the specific security needs and goals of the organization. A Virtual Private Network (VPN) is a secure connection between two or more devices that allows users to access internal corporate networks from outside of the organization. It provides secure remote access, but it does not provide granular access controls. On the other hand, Zero Trust Network Access (ZTNA) provides granular access policies that can be tailored to the individual user or device. This helps organizations to set more stringent access policies and reduce the attack surface of their networks. In general, ZTNA is a better option for organizations that require higher levels of security and control.
How Is Zero Trust Different from a Software-Defined Perimeter?
Zero Trust Network Access (ZTNA) is different from a Software-Defined Perimeter (SDP) in that it provides granular access policies tailored to the individual user or device. ZTNA allows organizations to set stringent access policies for users based on identity, device health checks, and other contextual information. This helps prevent unauthorized users from accessing sensitive resources and reduces the attack surface that attackers can leverage. SDP, on the other hand, provides a more secure perimeter-based model by creating a virtual tunnel for users to connect to an internal network. It is designed to provide an extra layer of security and control beyond what is available with a traditional VPN.
How does ZTNA help with Secure Access Service Edge?
Zero Trust Network Access (ZTNA) helps with Secure Access Service Edge (SASE) by providing granular access control that is tailored to the individual user or device. This allows organizations to control who is able to view or access certain resources based on user identity, device health checks, and other contextual information. This helps prevent unauthorized users from accessing sensitive resources, while also reducing the attack surface that attackers can leverage. Additionally, ZTNA can provide additional security measures such as user authentication and device health checks, which can help to further reduce the risk of a breach.
Can I use ZTNA to control access to the Public Internet with a remote workforce in large and small businesses?
Yes, ZTNA can be used to control access to the public internet with a remote workforce in both large and small businesses. By leveraging granular access policies tailored to the individual user or device, organizations are able to limit user access to certain public resources based on identity, device health checks, and other contextual information. This helps reduce the risk of data leakage, unauthorized access, and external threats. Additionally, organizations are able to set more stringent access policies to help prevent malicious actors from accessing sensitive information.
Conclusion
Zero Trust Network Access (ZTNA) is a cybersecurity strategy that enhances secure remote access by not requiring any ports to be open to the internet, thus reducing the risk of attacks. It is an advancement over traditional VPNs, integrating user identity verification, device health checks, and contextual data to enforce strict access policies. This approach is crucial in today's landscape of escalating cyber threats, as it minimizes unauthorized access and limits the attack surface. ZTNA offers benefits like reduced attack surface, centralized control over access policies, and granular, context-aware access permissions. It is applicable in various scenarios, including VPN replacement, vendor access, application access, and micro-segmentation. ZTNA is also instrumental in data protection and privacy, allowing for policies that restrict access based on identity, location, and device type. For organizations, adopting ZTNA means enhancing security while complying with data privacy regulations and adapting to a more digital, remote workforce. It is a key component of a broader Zero Trust strategy, essential for reducing compromise risks and creating a more secure network environment.



