Service Accounts
Lack visibility and monitoring
Stop privileged account abuse by restricting access to operational needs only - it's automated, agentless, and MFA-powered
"People in the domain admin group cannot do anything without MFA. That is game changing."

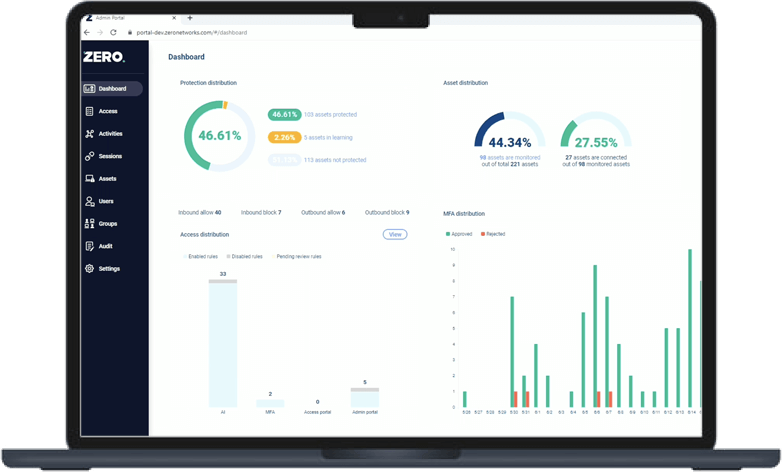
Zero Networks revokes logon rights for all admin and service accounts and then provisions them based on least privilege, enhanced by multi-factor authentication (MFA).
This blocks lateral movement even if credentials are stolen, and prevents Pass the Ticket, Golden Ticket, Kerberoasting, and other attacks.
Zero Networks’ patent-pending technology learns all logons for a recommended 30-day period, understands which service accounts and logon types are intended to be used on each asset, and automatically restricts logon rights and types to these assets.
Day 1
Learning Begins
Agentless, 1-hour deployment
Learning In Progress
Glean insights on account usage and eliminate inactive accounts
Day 30
Logons Restricted
Automatically prevent unauthorized access and lateral movement
Zero Networks enables IT teams to restrict admin accounts, permitting temporary logon to pre-approved assets only after MFA, and blocking all other logon rights.




 1990s |  2000s |  2010s |  Today |
|---|---|---|---|
| Password Vaulting | Tiered Model | MFA Enablement | Zero Networks Protect all identities with a click |
Governing access rights is notoriously complex
Time to value: Months, often years |
Time to value: 30 days | ||
















