Cybersecurity is the practice of protecting IT networks, devices, applications, and data from malicious activities such as data breaches and ransomware. The main goal of cybersecurity is to prevent unauthorized access and criminal usage of systems and data. A strong cybersecurity program incorporates technical solutions like multi-factor authentication, firewalls, network segmentation, and various detection and response solutions. Creating strong passwords and updating them often, keeping systems and applications up-to-date, and educating employees and users to be on the lookout for suspicious emails are some of the low-tech ways that organizations can keep their networks and their data safe.
Why is cybersecurity important?
The importance of cyber security is best illustrated by the fact that it has become a ubiquitous challenge–regardless of company size or location. In fact, smaller enterprises have become a bigger target due to poor resourcing and skill set. According to Verizon, 61 percent of data breach victims were small businesses. In today’s threatscape, the amount of effort required to get an effective defense up and running has become unattainable by most enterprises–large or small. Many organizations have neither the time nor the resources to implement technology to help automate some of these key functions. So they are trapped on the hamster wheel of pain, reacting without sufficient visibility and time to invest in gaining that much-needed visibility into cybersecurity threats.
And the cybersecurity industry isn’t giving anyone any good options. Despite the billions in venture money that has poured into security startups, the majority of new vendors focus on larger enterprises with bigger budgets. Today, big companies with million-dollar cyber budgets assemble a defense-in-depth strategy to block and mitigate a wide variety of attacks such as phishing, ransomware, DDoS, APT, and so on. What can today’s businesses do? Investing in a full suite cyber security stack would not only be cost prohibitive but with their limited resourcing, would also be unfeasible.
Key challenges in cybersecurity today
Today’s attacks broadly target endpoints, networks, and cloud resources. At a minimum, a comprehensive defense built from cybersecurity solutions requires at least a firewall, AV, SIEM, EDR, analytics, cloud security, and much more. Yet many firms lack basic controls. Some key cybersecurity trends: Small and medium enterprises, according to the BBB, rely mostly on firewalls (76%) and AV (81%)–but little else. In fact, the most common cyber defense measure behind technology, according to the same BBB survey, is employee training at 47%. Worse, existing tools are noisy and provide a siloed view: Organizations have point tools in place that were purpose-built to solve a specific problem but were not purpose-built to address cyber risk management in a holistic way. Existing security point tools flag threats and anomalies but fail to look at the enterprise as a whole, understanding the 100s of activities that take place each day and correlating it with a firm’s intrinsic risk.
Limited resources and expertise. Even having people to throw at security management may not be enough. They need to be the right people with expertise in confirming exposures, closing simple issues, and pulling the alarm to escalate to the investigations team. Reviewing events, setting up policies, and managing the system all take skills that come with training and time with the product. Clearly, this is not a skill set you can just pick up, and finding and keeping talented people is hard, so if you don’t have sufficient sophistication internally, that’s a good reason to check out a service alternative. For smaller firms, according to SANS, 55% percent of SMBs have one dedicated IT employee and one dedicated cybersecurity employee. Staffing numbers are about half of what they consider to be ideal.
Modern attacks focus on finding the weakest link in your security ecosystem and gaining an initial foothold in an enterprise network. Once on the network, they move laterally, patiently focused on achieving their mission. Thus, security is no longer just keeping the bad people out; it also requires the ability to detect and track every step an attacker has taken to search and traverse the network in pursuit of their ultimate goal. A key problem is the lack of segmentation–a basic part of the Zero Trust cybersecurity framework. For years, microsegmentation has been a critical objective. The idea of sequestering different parts of your infrastructure to block lateral movement has remained elusive due to its manual and time-consuming nature.
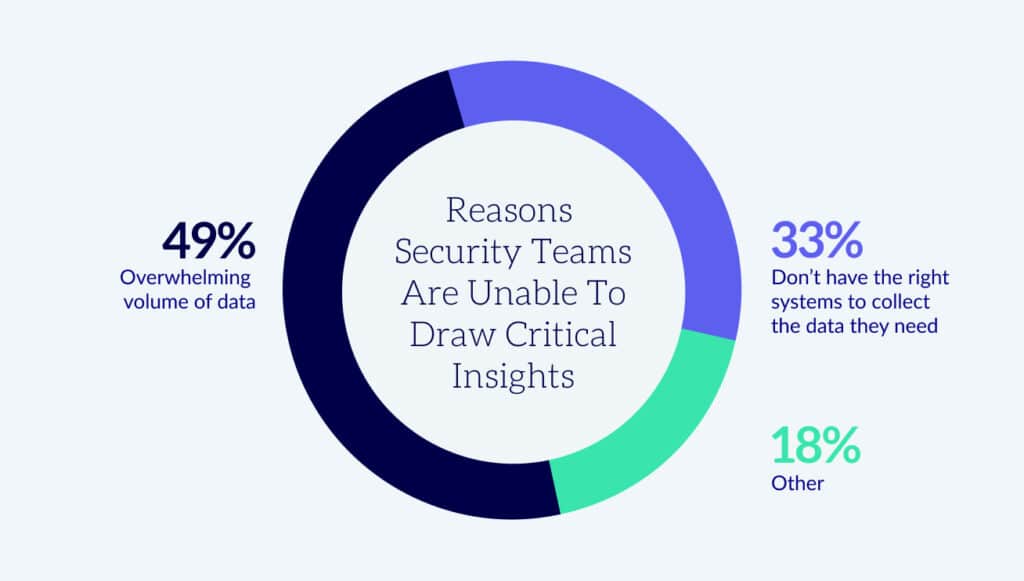
Data overload decimates SOC productivity. With a rapidly growing surface and data sources, security teams must incorporate too much data that fails to provide context to show how attacks unfold. Security teams are unable to obtain/draw critical insights from the large amount of data generated daily from their infrastructure--putting SOCs permanently one step behind attackers. A recent survey cited several challenges security teams face as data requiring analysis continues to proliferate:
- 49% said it is because of an overwhelming volume of data
- 33% aren’t collecting the data they need because they don’t have the right systems
Consequently, SOC team efficiency is at an all-time low. Security teams suffer from digital exhaust as thousands of alerts are sent to their SIEM dashboard. Understaffed, security teams are unable to triage each alert, succumbing to the belief that most of the alerts received are actually false positives.
The bad guys do their best to look normal. Low and slow attacks have become the new norm–even in DDOS attacks. Cyber criminals purposely take their time, spreading their malicious activity over the course of days, weeks, or months to avoid detection. By using the noise generated by benign operational activity as a backdrop, cybercriminals can blend in to day to day activity without ever getting noticed. As a result, security teams are unable to stitch together a meaningful attack progression of undergoing cyber campaigns within their organization from malicious alerts.
The Zero Networks solution
The next generation of cybersecurity technology and cybersecurity software must protect from all types of attacks using an easy, consolidated platform that gives organizations complete visibility into systems and full control over response. In Zero Networks’ vision, organizations are completely defended – with minimal effort. Zero Networks' approach simplifies and converges cyber defense so organizations can quickly and easily handle cyber-attacks and keep focus what they do best.
This means:
- Fast time to value: Zero Networks fully deploys and is fully operational in less than two hours.
- No training needed
- A single pane of glass for all threats
- No expertise needed: The Zero Networks platform defends organizations with the cloud generation in cyber security – giving them the ability to instantly identify, block and respond to attacks without the heavy burden of deep cyber expertise, the overhead of multiple products, and the complexity of managing a fast-evolving threatscape.



