TL;DR
Microsegmentation divides a network into isolated segments with their own security perimeters to prevent lateral movement of threats. Implementing microsegmentation improves security by reducing attack surfaces, though it requires granular visibility and control of network connections which can be challenging to do manually. Automated microsegmentation solutions like ZeroNetworks overcome these challenges by automatically isolating assets without agents or manual rules.
What Is Microsegmentation?
Microsegmentation (or Micro Segmentation) is a cybersecurity concept. It refers to the practice of dividing a network into very small regions called microsegments, usually up to a segment per machine.
The goal of microsegmentation is to reduce the attack surface of a network by isolating every element—all clients, workloads, applications, virtual machines, and operating systems—into its own protective barrier that cannot be penetrated by attackers. Segmenting the network in this way makes it virtually impossible for attackers to move laterally within the network and cause damage.
However, because a network can consist of thousands or even tens of thousands of elements, it can be extremely difficult to implement this type of segmentation manually. The following guide will help you understand why microsegmentation is important, how it works, how to implement it, its challenges, and its benefits.
Why is Microsegmentation important?
Microsegmentation is important because it improves network security by creating smaller segments or microsegments within a network. This makes it more difficult for attackers to move laterally within a network and increases the chance that they will be detected.
Additionally, microsegmentation can help reduce the blast radius of an attack, making it less likely that a large portion of the entire network will be compromised.
In fact, according to Gartner: “By 2026, 60% of enterprises working toward zero trust architecture will use more than one deployment form of microsegmentation, which is up from less than 5% in 2023.” In short, they’re predicting a 12-fold increase in just three years when it comes to microsegmentation adoption rates!
How Does Microsegmentation Work?
In a nutshell, microsegmentation works by creating small, distinct segments within a network (usually a segment per individual machine). By doing so, each segment becomes its own mini network with its own security perimeter. In a microsegmented network, attackers cannot move laterally within the network and reach their target. Even if an attacker breaches one segment, the others remain secure.
Ideally, microsegmentation should create a segment per host or machine. But to achieve that, traditional microsegmentation solutions involve installing an agent on every machine and then manually defining the network allow-list (who or what can connect to and from each machine).
Because of this, microsegmentation has not been a scalable option for cyber defense. That is until now with the introduction of Zero Networks Segment™️!
The Use Cases of and Benefits Microsegmentation

How to Implement Microsegmentation to Achieve Zero Trust
Implementing a microsegmentation strategy within your network security infrastructure can help your organization achieve Zero Trust. This is because microsegmentation isolates and protects all your assets from being compromised by attackers. What is Zero Trust? At a high level, Zero Trust is a security model that requires organizations to verify the identity of users and devices before granting them network access. You can read more about Zero Trust, and Zero Networks’ approach to it here.
The Challenges of Microsegmentation
A high level of visibility into your network and insights on what is needed and what is not needed is necessary to accomplish microsegmentation. This can be a challenge to implement manually, particularly if your network is always changing. In addition, microsegmentation requires a great deal of coordination and planning to be effective.
More FAQs Related to Microsegmentation
What is a Zero Trust Architecture
Zero Trust architecture is a security model that requires organizations to verify the identity of users and devices before granting them network access. In other words, it’s an approach to cybersecurity where organizations do not automatically trust anything inside or outside their network perimeters. In a Zero Trust environment, all entities must be authenticated, authorized, and constantly monitored for suspicious activity.
What is the purpose of microsegmentation?
The purpose of microsegmentation is to create smaller, isolated segments within a network that have their own security perimeter. This helps to reduce the attack surface of each segment and prevents attackers from moving laterally within the network. It also allows organizations to regulate traffic between segments, ensuring that only trusted connections are allowed.
What Is Least Privilege Access?
Least privilege access is a security approach that limits the number of system privileges assigned to users or applications on a network. This means granting only the permissions and access necessary to perform a task and no more. This helps to reduce the attack surface of the system, as attackers are unable to take advantage of any additional privileges they may have gained access to.
Does microsegmentation work for cloud networks?
Yes, microsegmentation can work for cloud networks. By leveraging virtualization technology, microsegmentation can be used to create isolated segments within the cloud environment, which can help reduce the attack surface of the entire cloud infrastructure. This is especially important in multi-tenant environments where resources are shared between different organizations. With microsegmentation in place, organizations can better secure their cloud network and protect their data.
What is the zero-trust security model?
The Zero Trust security model is an approach to cybersecurity focused on verifying the identity of users and devices before granting them network access. In a Zero Trust environment, all entities must be authenticated, authorized and constantly monitored for suspicious activity. This means that organizations do not automatically trust anything inside or outside their network perimeters. To achieve this level of security, organizations use access control lists (ACL s), firewalls, and microsegmentation to create smaller, isolated segments within a network that have their own security perimeter.
What is a network segment?
A network segment is a logical division of a computer network. It consists of a series of nodes connected by a communications link that forms part of the same broadcast domain. Segments are typically separated from one another using layer 3 (Network Layer) protocols such as IP routing. Network segments can be used to isolate traffic, reducing potential points of attack and enabling more granular access control. Network segmentation is often used in conjunction with microsegmentation to create smaller, isolated segments within a network that have their own security perimeter.
What is an example of microsegmentation
An example of microsegmentation is the use of a firewall or access control list (ACL) to create smaller, isolated segments within a network that have their own security perimeter. This approach works by allowing organizations to regulate traffic between different segments - only allowing trusted connections and preventing unauthorized access from outside the network. For instance, an organization could segment a web application from its internal databases, so that users can only access the web application and not its databases, reducing the attack surface of both components.
What is the need for microsegmentation
The need for microsegmentation is driven by the need to create smaller, isolated segments within a network that have their own security perimeter. This allows organizations to regulate traffic between different segments, ensuring that only trusted connections are allowed. By creating smaller, segmented networks, organizations can reduce their attack surface and protect against malicious actors who may try to gain access to sensitive data or resources. Furthermore, microsegmentation allows for better visibility and control over user activities within a network, making it easier to detect and respond to potential threats.
What is the difference between segmentation and microsegmentation
Segmentation and microsegmentation are both security practices that can be used to limit access to sensitive systems and data. The main difference between the two is the scope of the segmentation. Segmentation refers to dividing a network into several distinct parts, while microsegmentation applies further granularity by creating smaller, isolated segments within each part of the network. This allows organizations to enforce more granular access control, with stricter rules and restrictions on who can access what. Additionally, microsegmentation typically requires the use of a firewall or access control list (ACL) to enforce the segmentation.
What is the difference between microsegmentation and Zero Trust
The difference between microsegmentation and Zero Trust is that microsegmentation focuses on creating smaller, isolated segments within a network that have their own security perimeter, while the Zero Trust model is an approach to cybersecurity focused on verifying the identity of users and devices before granting them network access. Microsegmentation relies on the use of firewalls or access control lists (ACLs ) to create the segmentation, while Zero Trust relies on authentication and authorization measures such as multi-factor authentication (MFA), identity and access management (IAM), continuous monitoring, and strong passwords.
What about using microsegmentation with containers
Microsegmentation can also be used with containers in order to secure access to applications and resources. Containers are an increasingly popular way of deploying applications and isolating them from each other, making them a great target for microsegmentation. By leveraging the isolation of containers, organizations can create smaller, more secure segments within their network that are difficult to penetrate. This allows organizations to control access to their applications and resources, ensuring that only trusted users are able to access them.
How does microsegmentation help protect East-West Traffic and North-South Traffic?
Microsegmentation can help protect East-West traffic and North-West traffic by creating smaller, segmented networks that have their own security perimeter. This allows organizations to regulate traffic between different segments, preventing unauthorized access from outside the network. By segmenting East-West traffic (traffic within a data center) and North-West traffic (traffic between data centers), organizations can reduce
How can microsegmentation help with compliance and security policies?
Microsegmentation can help with compliance and security policies by allowing organizations to create smaller, isolated segments within a network that have their own security-enforced perimeter. This allows organizations to enforce access control and authentication rules on specific parts of the network, ensuring that only trusted users and devices are able to gain access. By segmenting the network into smaller, more secure sections, organizations can ensure that their data and systems remain secure and compliant with industry standards.
What is the difference between microsegmentation and traditional network segmentation?
The primary difference between microsegmentation and traditional network segmentation is the level of granularity. Traditional segmentation divides a network into several distinct parts, while microsegmentation applies further granularity by creating smaller, isolated segments within each part of the network. This allows organizations to create more secure, tightly controlled segments with stricter rules and restrictions on who can access what. Additionally, microsegmentation typically requires the use of a firewall or access control list (ACL) to enforce the segmentation, whereas traditional segmentation does not.
Can microsegmentation help with the movement of threats?
Yes, microsegmentation can help with the movement of threats. By making use of smaller, segmented networks within a larger network, organizations can create a secure perimeter between different segments and restrict access from outside sources. This helps to prevent malicious actors from moving freely between segments and limits the potential scope of any attack. Additionally, microsegmentation can be used in combination with other security measures to further reduce the potential for malicious activity.
Does microsegmentation have any impact on the operation of premises data centers?
Yes, microsegmentation can have an impact on the operation of premises data centers. By segmenting the network into smaller, more secure sections, organizations can reduce the risk of attacks on their data centers and increase security for their systems and applications. Additionally, microsegmentation allows organizations to create different access control policies for each segment to ensure that only authorized users have access to specific parts of the network. Additionally, microsegmentation can be used in combination with other security measures to further reduce the potential for malicious activity.
Additional Resources
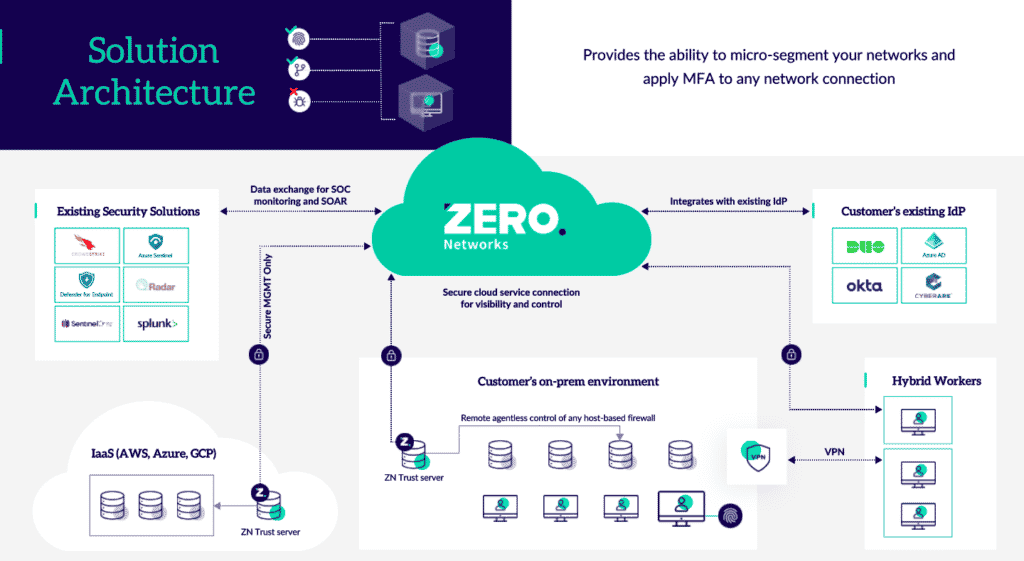
The Zero Networks Solution
Zero Networks provides an automated microsegmentation solution that adapts to your environment, keeping only the necessary connections between machines open. By leveraging adaptive MFA (Multi Factor Authentication), normal usage for non-admin users is uninterrupted (attackers do not use that to spread), while the rest (admin users) require MFA for temporary access.
Zero Networks virtually eliminates your network’s attack surface with no manual segmentation or rule manipulation, and no agents. The benefits of automated microsegmentation:
- Isolate everything (down to the individual machine) with a single click and no friction
- Prevent 99.9% of attacks. Stop lateral movement without interrupting normal network traffic
- Scalable for any size organization, without the need for agents or manual operation
- Streamline security operations; reduce the cost of NACs, internal firewalls, IPS and manual ACL-based microsegmentation
- Stay compliant with cyber insurance policies
About Zero Networks
Microsegmentation means that every module in the environment should only be able to access the information and resources necessary for legitimate purposes. Great idea – in theory – that few organizations practice. Sadly, past efforts at microsegmentation required cumbersome agents, hair pinning, or expensive professional services. Zero Networks, instead, found a new paradigm that proves that microsegmentation can be fast, easy, effective, and deployable by anyone to get military grade security. Reduce the risk of breaches to almost zero with Zero Networks' MFA-based microsegmentation solution. Request a demo.




