TL;DR
Until today, no native or open-source solution was available to protect LDAP - yet it is a critical service that attackers commonly exploit in domain environments.
LDAP Firewall is a new open-source tool by Zero Labs that lets you control and audit LDAP requests to enhance the security of Domain Controllers, mitigate LDAP-based attacks (such as sAMAccountName spoofing and BloodHound) and tightly control access to Active Directory. All it takes to get started is to run the LDAPFW executable and configure rules to suit your needs (we provide a few examples for mitigating common attacks later in the article).
You can download LDAP Firewall from our GitHub repository.
Stay tuned for part 2 of this article that will deep dive into our research around LDAP and the inner workings of the LDAPFW.
Background
In the Windows environment, the Domain Controller is king - holding the (literal) keys to the kingdom. And while we would love to safeguard the DC servers by locking down all network ports, the great paradox of Windows network security is that many services must be open and accessible to all users for the environment to function properly.
The most vulnerable of these are the “multiplex” ports, which are used legitimately by many hosts, but that also include dangerous functionality baked right into the protocol. These are the RPC, SMB, and LDAP protocols.
Previously we released the RPC Firewall to allow defenders granular configuration of permitted remote functions, thus preventing RPC-based attacks. Now we jump to the next level of DC security by tackling LDAP.
LDAP 101
Lightweight Directory Access Protocol (LDAP) is used in Windows domain environments to interact with the Active Directory schema. It is commonly used to query information about users and groups (e.g., get the list of members in a distribution list when you compose an email using Outlook). As such, the LDAP ports (389, 636) must be left open on the Domain Controllers and be accessible to all users of the domain for the environment to function.
After performing a successful connection, different LDAP operations can be used to read or modify entries in the schema. This is somewhat similar to SQL queries, where you select values or update the database.
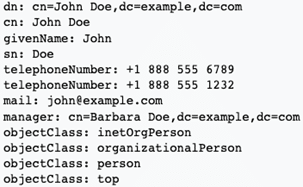
A Distinguished Name (DN) is used as the unique identifier for each entry, which acts as a sort of "path" to it. Each entry has a set of attributes, each one with a name and set of values.
Example entry (taken from Wikipedia), with its DN and set of attributes:
How LDAP Firewall Works
In the Windows OS, only limited logs are available for LDAP. It is also impossible to natively harden the LDAP configuration (apart from manually managing user permissions).
The LDAP Firewall inspects incoming LDAP operations - which are used to read or modify entries in the Active Directory schema - and allows or blocks the request based on the configured rules. The operation also gets written into the Windows Event Log, including the action taken and other relevant fields (Distinguished Name, attributes, OID etc.).
Preventing Attacks with LDAPFW
This section describes a couple of common LDAP-based attacks that are mitigated with the LDAP Firewall. Sample config.json files for the LDAPFW can be found in the example_configs folder of the GitHub repository.
sAMAccountName spoofing
The sAMAccountName spoofing attack allows escalation of privileges from a standard user by combining 2 vulnerabilities. The first is Name Impersonation (CVE-2021-42278), where a new computer account is added with a trailing “$” sign in their name. Combined with KDC bamboozling (CVE-2021-42287), attackers can impersonate Domain Controller accounts.
The LDAP Firewall can be configured to block all Add operations to completely prevent Name Impersonation (CVE-2021-42278) and thus defend against sAMAccountName spoofing.
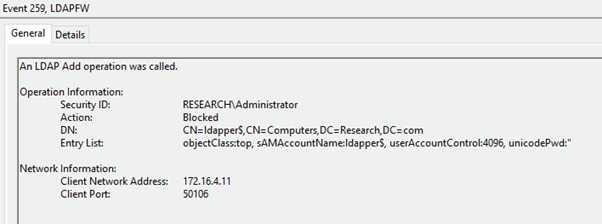
Audit of an LDAP Add operation being blocked (produced using the Ldapper addComputer command)
BloodHound
BloodHound is an open-source tool for mapping and identifying vulnerabilities in Active Directory, commonly used by adversaries to reveal attack paths in the environment. It gets much of its data by directly querying the Domain Controller using LDAP.
BloodHound can be mitigated with the LDAP Firewall by blocking LDAP searches on uncommon attributes (such as admincount, userpassword and msds-allowedToDelegateTo). In case these attributes are used in legitimate LDAP queries, they can be allowed from specific IPs or users.
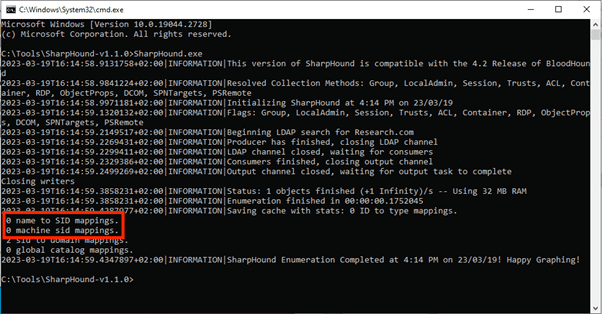
SharpHound (BloodHound’s collector) unable to obtain entities using LDAP
Summary
Zero Network’s LDAP Firewall continues the journey of the RPC Firewall to completely locking down the Domain Controllers and protect against previously unpreventable attacks – without impacting daily operations.
Both the RPC & LDAP Firewalls are open source and can be used for free and are also available through Zero Networks Segment automated managed service.
If you want to see this in a demo as part of Zero Networks Segment, our experts would love to show you how easy it is to turn on Active Directory protection in a click.
For any questions, issues, or simply to shout out, join our new -273°C Slack channel where the community shares best practices and helps build better defenses using open-source tools. We are also available at support@zeronetworks.com.



