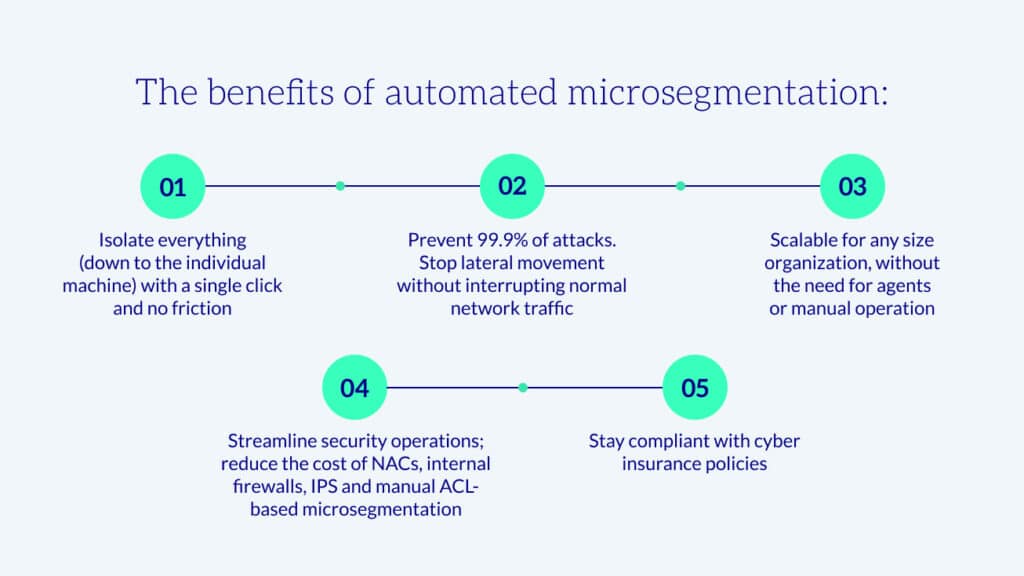
Automatic microsegmentation is KEY!
According to Network World, ”one of the big challenges with segmentation is you have to know what to segment.” At Zero Networks, we knew this was true. That’s why we created automated microsegmentation solution that learns and creates the optimal segmentation for your organization. Many other microsegmentation vendors require organizations to conduct their own analysis of network traffic and manually build all the segmentation rules themselves. This is time consuming for analysts and takes away from other key priorities.
Without microsegmentation, attackers can infiltrate an organization and spread laterally throughout the network with ease. AT&T even noted this here, “Many organizations have found traditional detection and prevention technologies are no longer sufficient to mitigate the threats posed by opportunistic actors”. The takeaway? Traditional defenses and network segmentation are not enough. This has led to the creation of microsegmentation solutions across the industry.
Organizations must enhance their layers of defense by adding microsegmentation. No other solution is effective at preventing attackers from spreading. But even so, imagine having to build all those rules by hand…can we say #impossible. So, to make microsegmentation feasible, automation is a MUST.
Agentless microsegmentation = less overhead and complexity
NIST states in SP800-207 Zero Trust Architecture: “Alternatively (or additionally), the enterprise may choose to implement host-based micro-segmentation using software agents or firewalls on the endpoint asset(s), These gateway devices dynamically grant access to individual requests from a client, asset or service.” This is why at Zero Networks we have implemented MFA based Just-In-Time (JIT) access policies. These policies grant access per individual request using built-in operating system firewalls, which doesn’t require an agent on every asset. Our microsegmentation solution is designed to cover all server, clients and even OT/IOT devices, to enable microsegmentation across the enterprise.
To often in our conversations with customers, we hear “do I need to deploy *another* agent”. Organizations are feeling the agent-bloat. There is even a new space forming called ‘cybersecurity asset management’ to help organizations identity which assets are in which cyber tools/solutions and show gaps across the tools. Other microsegmentation vendors typically require an agent adding to the bloat customers already struggle with. This is why we believe that it’s even more important to be agentless: to reduce complexity for organizations and increase the performance of assets, all without requiring a single additional agent.
There also exists microsegmentation tools that operate at the network level vs the endpoint/host. These microsegmentation tools have a few gaps in that assets that leave the network, eg use at home or the coffee shop are not protected wherever they go. They must be connected to the network in which the Microsegmentation tools are deployed. With Zero Networks, assets are protected wherever they roam.
Meet cyber insurance requirements and reduce risk
With Zero Networks deployed, it’s easy for a company to meet cyber insurance requirements. In fact, most of our customers exceed the normal requirements, which significantly reduces risk and ultimately saves on the cost of insurance premiums. According to the US Government Account Office, “The cost of cyber insurance is based in part on the frequency, severity, and cost of cyberattacks, all of which have been increasing. The uncertainty about future threats also plays a role, and insurers have become more selective about who and what gets covered. In our 2021 report, we found that a number of insurers reduced coverage limits or increased premiums for higher-risk organizations and industries, such as academic institutions or the health care and public sectors.”
One of the latest requirements we have heard from our customers is that all privileged access requires MFA. We know MFA can greatly reduce the chance of a successful attack which is why this requirement has started to creep in with various insurance vendors. Other microsegmentation vendors have focused on the rules engines which do not provide MFA based JIT access to meet this requirement. With Zero Networks MFA based JIT access organizations can easily meet this requirement which can help reduce the cost of insurance or even just allow the renewal of the policy.
Segmenting OT/IoT was impossible
Operational Technology (OT) and Internet of Things (IoT) create a unique challenge for security organizations. Businesses need them to run the business and digital transformation is driving companies to update and automate their businesses using these technologies. These technologies have limitations. They are typically embedded software devices withs limited to no security functionality, e.g. you might not even be able to change the admin username. You can’t deploy existing security software to these devices like anti-virus or endpoint detection and response (EDR). Traditionally, organizations would turn to network segmentation to secure these devices but introduces more cost and complexity and ultimately risk from misconfiguration that opens access when it's not supposed to be open.
Network World stated “If you can properly implement microsegmentation, you can add a layer of security between IoT devices and other sensitive resources without poking holes in your firewall”. Microsegmentation vendors can provide this by limiting access to/from endpoints/assets and OT/IoT devices. This can allow the business to provide that digital transformation while increasing security. But there still remains a gap. Even with limited access, there is still access to these devices for administrative purposes. Zero Networks provides MFA based JIT access for administrative purposes to OT/IoT access as well. Now, even if the attacker gets is…assume breach… they won't be able to get administrative access to the OT/IoT devices.
Summary
We can see from reports that attacks are not slowing, Forbes even noted “In 93 percent of cases, an external attacker can breach an organization's network perimeter and gain access to local network resources”. Once the attackers are in, they have free reign across the network. Microsegmentation solutions have helped but at a higher operational cost to organizations. Our goal at Zero Networks is to increase the ability to stop the spread if an attacker gets in without increasing the human cost to the organization.



