This post is an executive summary of our deep dive analysis of the SolarWinds supply chain attack. This touches upon the following subjects:
- An overview of the attack
- Understand why security mechanisms failed
- Recommendations
Attack Overview
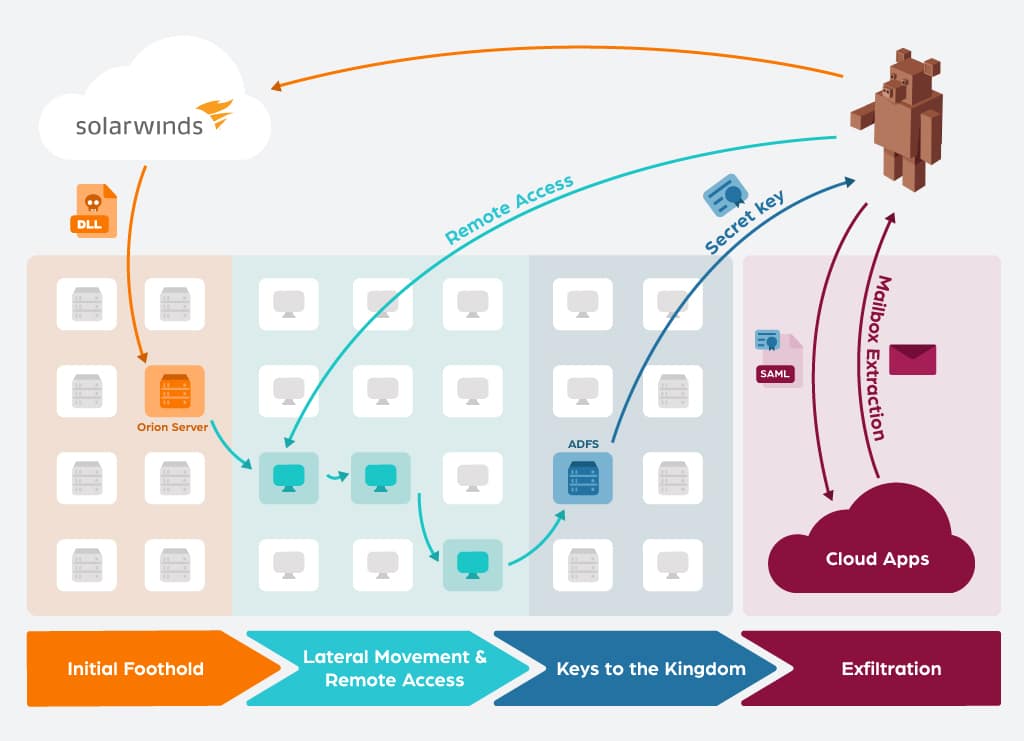
This is a supply chain attack, where a single technology or vendor is compromised in order to get access to their customers or users. In this case, the adversary was able to inject a backdoor into one DLL in SolarWinds’ Orion product (dubbed SUNBURST or Solorigate), which was then delivered through software update to roughly 18,000 organizations. Another vector of attack, which may even belong to a second actor, enabled similar access by using webshell as a backdoor (dubbed SUPERNOVA). The adversary then chose specific organizations to compromise further, tailoring the attack for each victim. While each victim may have suffered a different attack, in general, the actions of this attack can be broken down into four phases:
- Initial Foothold: After a dormant period of about two weeks (which helped in evading detection), the backdoor code sprung into action, communicating with the C2 infrastructure.
- Lateral Movement & Remote Access: Attackers stole credentials to move laterally, until reaching a high value asset they desired (ADFS server in most cases). The attackers favored “legitimate” remote access to get back in, and removed their own backdoors and tools when possible.
- Keys to the Kingdom: A compromised ADFS server gave the attackers the secret keys to impersonate any user in the organization (including bypassing MFA) .
- Exfiltration: Cloud applications (such as Office365) were accessed using forged SAML tokens, usually to export a target users’ email account.
Why Security Failed?
Given that this attack was ongoing for at least 10 months, why did security mechanisms not discover it?
Lack of budget? Probably not, as breached companies had a big security budget with the best security tools available.
Taken from NETRESEC
Lack of talent? Definitely not! Breached companies include FireEye and Microsoft, which have the best security minds money can buy.
Because it’s an advanced attack? This attack is the work of a patient adversary, with the means to orchestrate a sophisticated operation. However, no zero-days were disclosed, nor any novel technique. In fact, many techniques utilized for persistence and lateral movement are classic textbook tactics.
As a security company, we believe that the security industry as a whole is too invested in detection mechanisms as opposed to prevention. Many security products are in the detection business, responsible for producing security alerts, leaving the investigation, response and containment to the security team. This attack no doubtedly tripped over some wires, but was probably missed by security teams (including the best security teams in the world) who have to investigate and respond to hundreds, if not thousands of alerts per day.
Recommendations
Almost any major cybersecurity breach involves stolen credentials and lateral movement. This phase is where defenders have the best opportunity to stop and contain such attacks. Still we see ransomware attacks spread in this manner in hours, or stealthy attacks roam free undetected, in this case for months. Organizations should invest more in prevention oriented security. This would shift the burden of stopping attacks to the security products while the security team has a “breathing space” to investigate. For example, imagine that each abnormal network access in the organization would force users to strongly authenticate themselves, otherwise a high fidelity alert is produced. In this case, such an attack would have been stopped dead in its tracks. The deep dive offers more detailed recommendations.
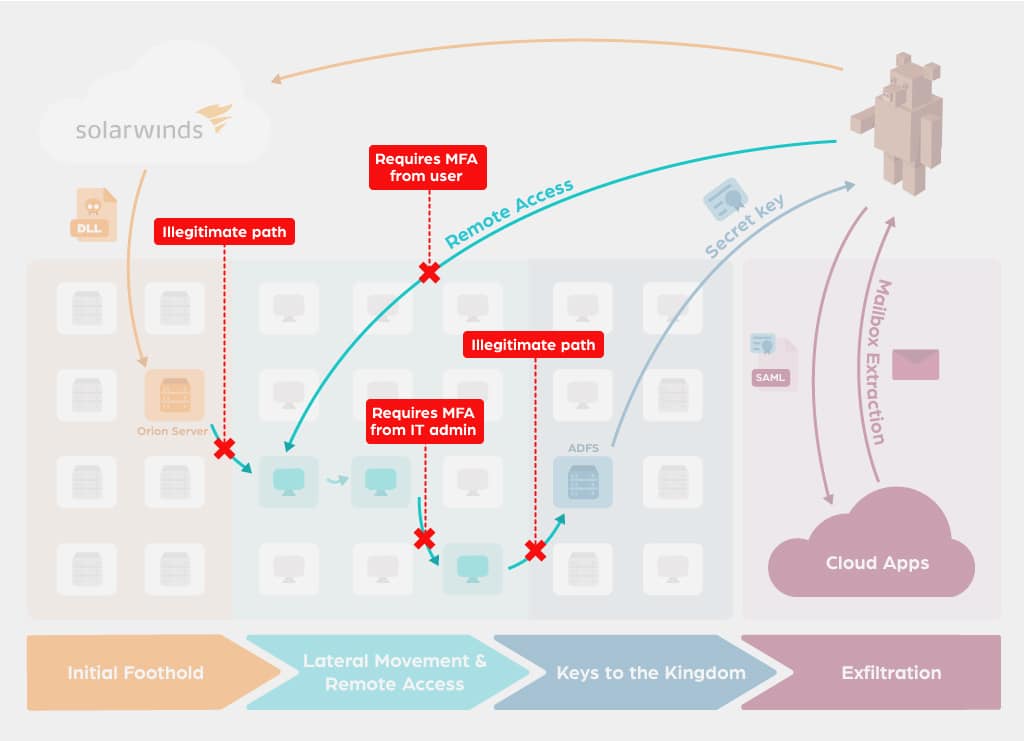
The Zero Networks Approach
With our Access Orchestrator it is easy to prevent attacks, from advanced threats to simple yet devastating ransomware. The Access Orchestrator blocks all network access apart from legitimate business activity. Its self service approach allows application owners and users to quickly get access to resources when needed, without opening up the entire network.
This least privileged networking approach makes sure the network is locked down and attackers are locked out. Reaching a least privilege networking stance for every asset in the organization with existing tools and processes is almost impossible, which is why we opened Zero Networks. See how it works, get a demo now.



