Operational Technology (OT) and Internet of Things (IoT), commonly referred to as OT/IoT, present unique security challenges to customers of all sizes. They are a required technology for businesses to operate and typically have very little to offer in the realm of security protections. Many of these devices are being connected to corporate networks to integrate with other business applications to enhance the performance of the business. In this blog, we will discuss some the challenges and how Zero Networks can help protect those device with a new capability.
The Problem
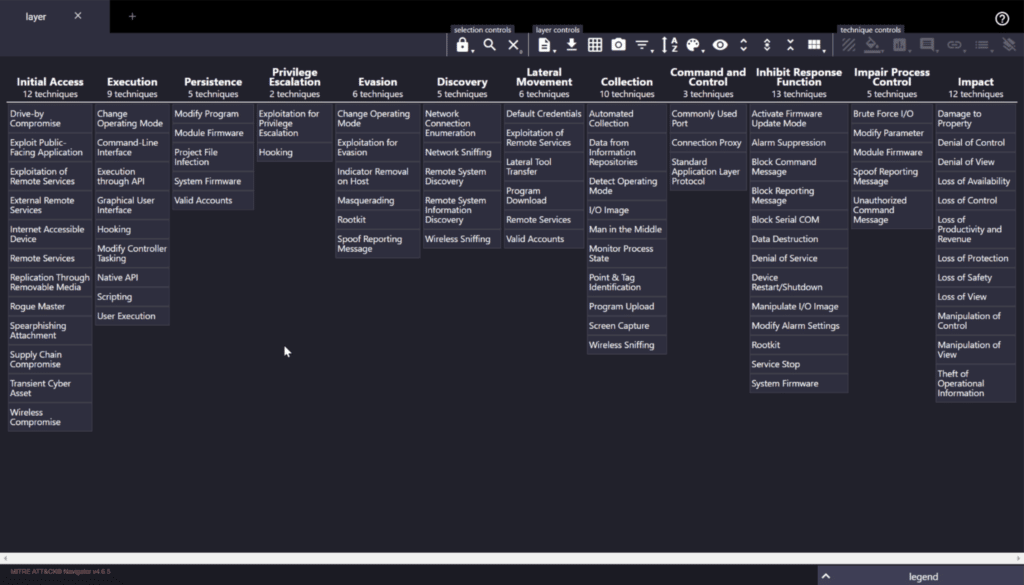
In 2017 an attack was discovered that targeted and Industrial Control System (ICS). This malware was known as Triton. The attackers leveraged a workstation that had access to ICS and learned the ICS make and model. They developed malware specifically for that ICS and deployed it to the device. Ultimately, the attackers were discovered before any harm was done, but this shows how and the typical attack pattern for OT/IOT happens. MITRE released an ATT&CK Framework for ICS in 2020. The tactics have the same pattern as other ATT&CK frameworks but the techniques differ a bit since OT/IoT are different from other common networked devices. There is also less of them because OT/IoT typically have less of a surface (apps, and operating system capabilities). Here is a view of the framework via the Navigator web provided by MITRE:
The Solution
How do you protect OT/IoT devices that have less capabilities? The devices don’t typically have full operating systems so tools like Endpoint Detection and Response (EDR) or Anti-virus can't be installed. Some have embedded firmware/software, like a printer or camera, which doesn’t even have the ability to enable a firewall. Detection tools typically require hardware packet level inspection which is cumbersome to deploy.
The only real prevention solution is network segmentation. Many organizations have segmented these devices using various methods like VLANs, dedicated network segments and deploying hardware firewalls to limit traffic between them. This is expensive to do throughout the organization plus the operational cost of ensuring only the right traffic is passing in the correct directions.
Zero Networks released a new software defined solution to protect OT/IoT devices that can reduce both the hardware and operational costs. The solution also prevents attackers from getting access to the OT/IoT devices in the event they do get into the environment. The solution blocks access to OT/IoT devices from all assets (Windows, Linux, Mac) which is typically the initial foothold an attacker would use to access them. When legitimate access is needed, the user is prompted for MFA and once MFA is passed then an outbound allow rule is created just in time (JIT) to allow access from the source endpoint to single requested OT/IoT device. The rule is then removed after a time period based on the MFA policy removing the access to prevent long term unnecessary access.
This can also be applied to devices like switches, printers, VoIP phones, etc to protect these devices from attacks.
The Final Word
In summary, it is critical to prevent attackers from spreading to OT/IoT devices. A key challenge in protecting OT/IoT environments is having to use one set of security products for IT protection and another for OT/IoT security. This complicates matters tremendously. With Zero Networks, it doesn’t matter—infrastructure is infrastructure. We built the capability to be agnostic by design to ensure simplicity and effectiveness. In this blog, we shared a brief overview of the problem and how Zero Networks is innovating to create new solutions to stop attackers cold.



